HTTP and HTTPS proxies: a complete guide to how they work, their differences, and how to use them
28.08.2025Basics of Protocols
HTTP, or Hypertext Transfer Protocol, is the foundation of data exchange on the web. It enables communication between your browser and a web server, allowing information to be transmitted. When you enter a URL and press "Enter," your browser sends a request to the server via the HTTP protocol. The server then responds to the request by sending back the required web page. This exchange happens at remarkable speed, letting you see content almost instantly.
However, it is important to note that HTTP does not guarantee data security. Information is transmitted in plain text, making it vulnerable to interception. Malicious actors can easily monitor your activity on websites or even manipulate data before it reaches you.
HTTPS, which stands for Hypertext Transfer Protocol Secure, is an enhanced version of HTTP. It adds an additional layer of protection through encryption, safeguarding the data transmitted between your browser and the server. When connecting to a website with HTTPS support, a digital certificate exchange takes place to verify the server’s authenticity. This ensures you are interacting with a legitimate resource rather than a fraudulent one.
What Are HTTP and HTTPS Proxies
HTTP proxies and HTTPS proxies are servers that act as intermediaries between the user and an online resource. They receive requests from the client, forward them to the target server, and return the responses back.
The key differences lie in how they process traffic and the ports they operate on. Let’s look closer.
HTTP Proxy:
Handles standard HTTP traffic. Data is transmitted in plain text, making it vulnerable to interception. Typically operates on port 80.
HTTPS Proxy:
Handles secure HTTPS traffic. Data is encrypted using SSL/TLS, ensuring security and confidentiality. Typically operates on port 443.
Additional Differences:
- Privacy level. An HTTPS proxy provides a higher level of privacy by encrypting data, while an HTTP proxy transmits it in plain text.
- Performance. An HTTP proxy may be faster in some cases since it does not require extra resources for encryption/decryption. However, this comes with a risk of data leakage.
- Website compatibility. Some websites require HTTPS access, which an HTTP proxy may block. HTTPS proxies, on the other hand, can process these requests without issue.
Types of HTTP/HTTPS Proxies
A quick and clear overview of HTTP/HTTPS proxy types.
Transparent Proxies
These proxies do not hide your IP address and do not modify requests. They are often used in organizations to manage access and optimize network performance. However, they do not provide anonymity and can be easily blocked.
Elite Proxies
Elite proxies completely hide your IP address and do not reveal that a proxy connection is being used. This makes you virtually invisible to websites, making them the best choice for those who seek complete privacy.
Anonymous Proxies
These proxies hide your IP address from websites, but the web server still knows the request is coming through a proxy. They provide a higher level of privacy but may run slower compared to transparent proxies.
Distorting Proxies
Distorting proxies alter your IP address to a random one, creating the illusion that the request originates from another region. While they help protect privacy, they are less reliable since they are easier to detect.
Use Cases and Recommendations
Where and how are HTTP/HTTPS proxies used, and who needs them?
For Developers and Testers
Developers and testers use proxies to monitor how their applications communicate with websites. Proxies allow them to view all requests and responses, which helps identify and fix errors. The best choice here is anonymous or transparent proxies, which allow testing without IP blocks.
For Process Automation and Data Collection (Web Scraping)
For collecting data from websites (web scraping), proxies are especially useful. They hide your real IP address, helping bypass restrictions and anti-bot protections. Elite or anonymous proxies work best here, as they allow data collection without the risk of being blocked. This is convenient for competitor analysis or price monitoring.
For Corporate Infrastructure
In offices, proxies are used to control access to internet resources, filter unwanted content, and optimize networks. This helps protect employees and speed up internet performance. Transparent proxies are an excellent choice for companies since they are easy to configure and manage, and can also cache data to speed up loading.
Choosing Between HTTP and HTTPS Proxies
When choosing between HTTP and HTTPS proxies, it’s important to understand your goals. The main difference lies in the level of data security and encryption. To make it easier, here’s a full comparison:
Security Level
The main distinction lies in how data is processed. An HTTP proxy works with unencrypted traffic, making it vulnerable to interception. For example, if you send confidential information via HTTP, attackers can easily obtain it. An HTTPS proxy uses TLS/SSL encryption. This creates a secure “tunnel” for data, and even if someone intercepts the traffic, they cannot decrypt it without the access key.
Performance
When it comes to speed, keep in mind that encryption requires additional resources, which can slow down an HTTPS proxy. If you are using outdated hardware or working with heavy workloads, this impact may be noticeable. However, modern technologies and optimized encryption significantly reduce delays, and in most cases, the speed difference between HTTP and HTTPS is minimal.
Quick Comparison
Encryption: HTTP: none. HTTPS: enabled (TLS/SSL).
Security: HTTP: low. HTTPS: high.
Usage: HTTP: caching, bypassing simple blocks. HTTPS: protecting personal data, anonymous browsing.
Traffic Handling: HTTP: works with HTTP traffic. HTTPS: works with HTTPS traffic.
Which Proxy to Choose
HTTP proxies are best suited for tasks where speed matters more, such as caching content or basic web scraping. They do not require additional encryption resources, ensuring minimal delays.
HTTPS proxies are preferable if your task involves protecting personal data or anonymous browsing. They provide a high level of security, which is especially important when dealing with confidential information.
Setting Up HTTP/HTTPS Proxies
For Windows Users
- Go to network settings. Right-click on "Start" and select "Network Connections." Then navigate to the "Proxy server" section.
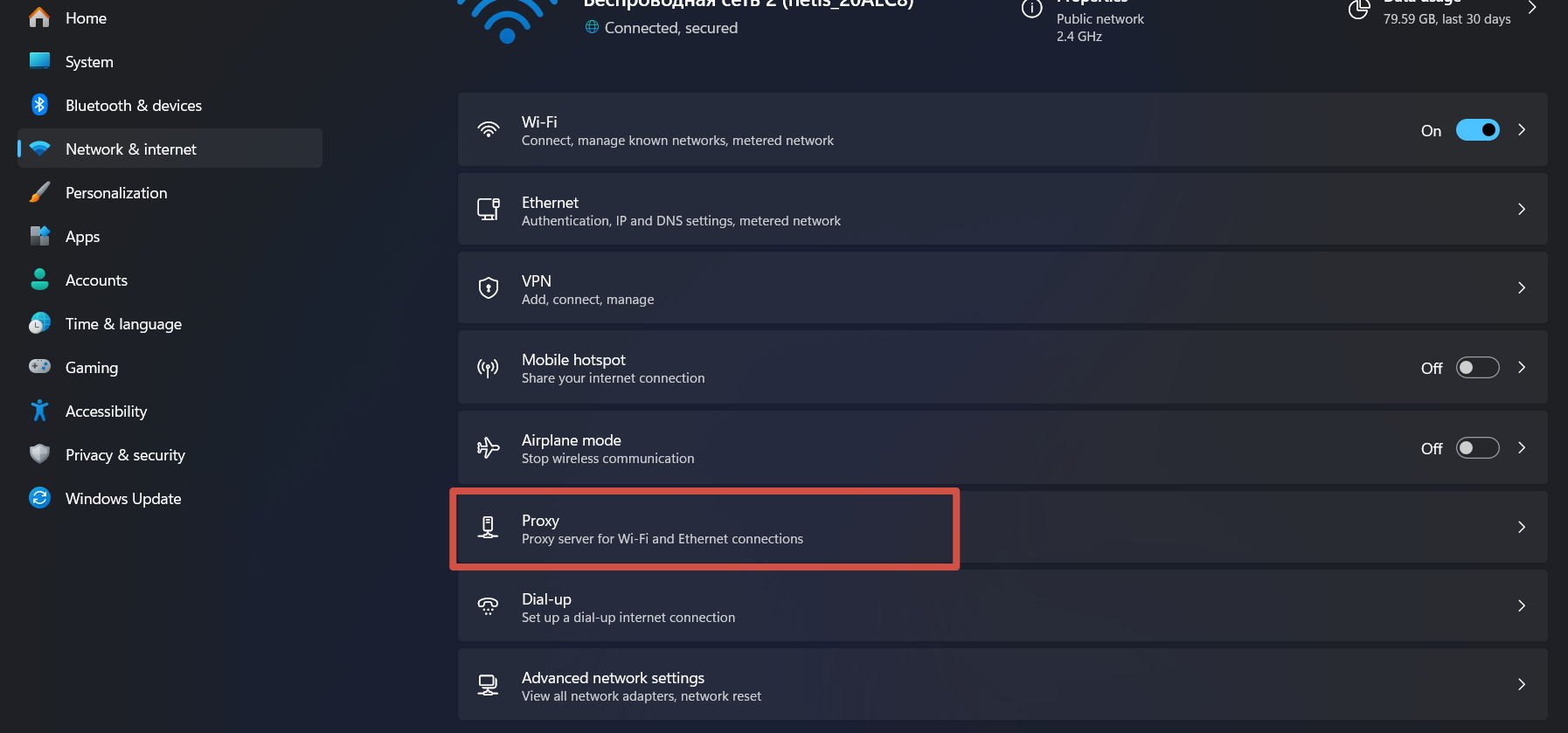
- In the section, choose "Use a proxy server" and click on it.
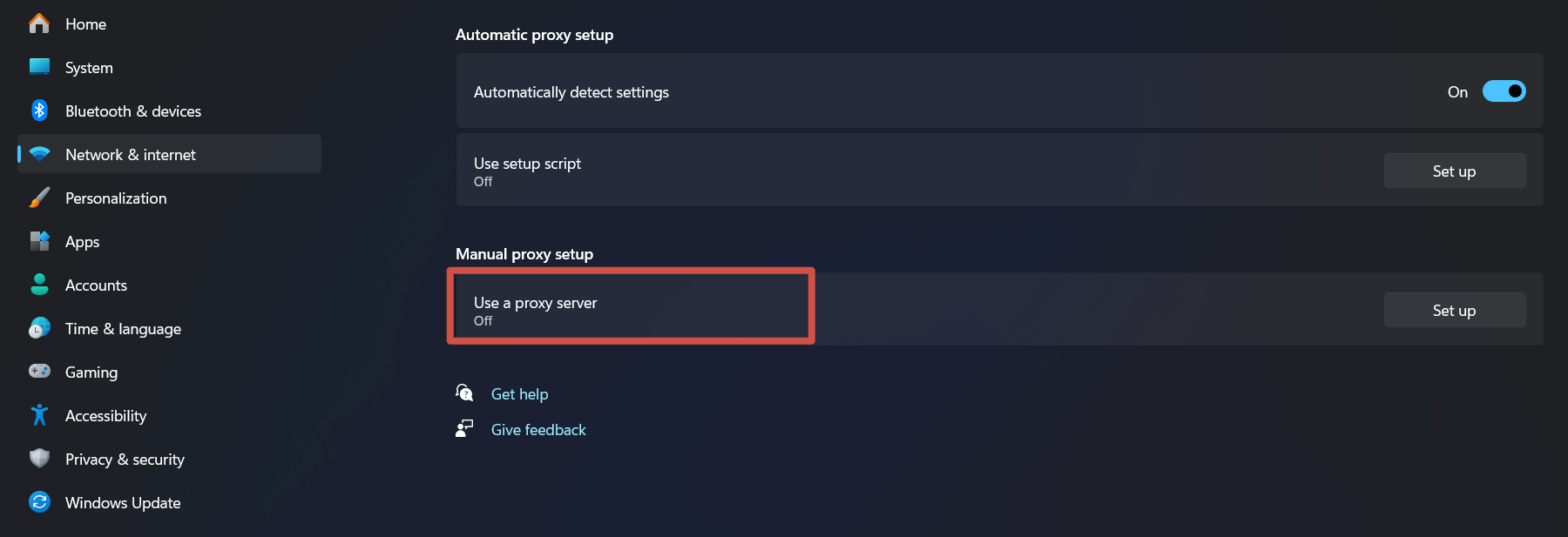
-
Next, enter the address and port of your HTTP proxy. If authorization is required, also provide your login and password.
-
Save the changes.
For MacOS Users
-
Click on the Apple icon in the corner of the screen. Select "System Preferences."
-
In the opened menu, choose "Network."
-
If you are using Wi-Fi, click "Wi-Fi" in the left panel and press the "Advanced" button. This opens additional settings.
-
Now select the "Proxies" tab.
-
Check the box next to your chosen proxy type. Enter the IP address and port provided by your service.
-
Save the settings.
Where to Find Reliable Proxies
When it comes to finding quality proxy servers, Belurk offers access to high-class proxies that meet all your requirements.
One of the key advantages of Belurk is reliability. We work only with verified proxy servers that ensure stable performance and high data transfer speed. In addition, you can sort proxy servers by various criteria, including country, speed, and other important parameters.
Belurk’s user-friendly interface makes managing proxy servers as simple as possible. Users can easily configure and control their connections without hassle. Our highly qualified specialists are always ready to provide fast technical support and help you with any questions in the shortest possible time.
Try belurk proxy right now
Buy proxies at competitive prices
Buy a proxy